VPC
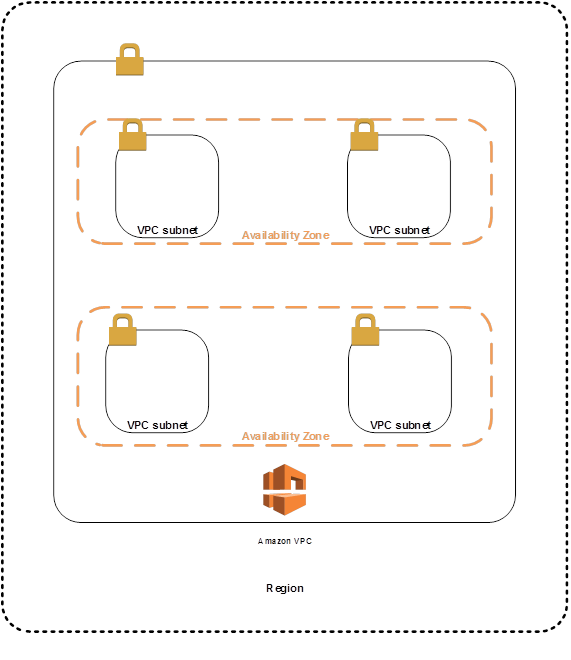
Whole networking in AWS starts with VPC. Virtual Private Cloud (VPC) is actually a virtual network. It is logically separated from other virtual networks in the AWS and it is assigned to one Region. You can specify an IP address range for the VPC, add subnets, associate security groups, network access lists and configure routing tables. All this to control your network traffic within AWS and traffic going outside.
Subnets
As mention above VPC spans all the Availability Zones in the Region, however subnet is created per AZ (in VPC). When you create a VPC you have to specify IP range (CIDR block). When you create a subnet, you specify the CIDR block which is a subset of the VPC CIDR block.
The first four IP addresses and the last IP address in each subnet are not available for usage and cannot be assigned to an instance. For example, in a subnet with CIDR block 10.0.0.0/24, the following five IP addresses are reserved:
- 10.0.0.0: Network address.
- 10.0.0.1: VPC router.
- 10.0.0.2: DNS server.
- 10.0.0.3: Reserved by AWS for future use.
- 10.0.0.255: Network broadcast address, not supported in a VPC, therefore is reserved.
Routing tables
Routing tables are same concept as you know them from any network device, simply routes to network destinations. Routing tables are set at subnet level. A route table can have many subnets, but a subnet can belong to only one route table. By default, newly created route tables will have the CIDR of our whole VPC defined. This means that traffic from anywhere within VPC is allowed and routed (also between subnets). If access to the Internet is needed you have to add a route via gateway.
Internet gateway
An internet gateway is a horizontally scaled, redundant, and highly available VPC component that allows communication between instances in your VPC and the internet. It therefore imposes no availability risks or bandwidth constraints on your network traffic.
As name implies Internet gateway allows you to connect to the Internet, details are explained below.
Public subnets
A public subnet is a subnet that has access to the Internet. It requires a public IP assigned to an instance and route added to route table via Internet gateway (or VPN or Direct Connect). Regardless the method direct access to the Internet from VPC’s CIDR block is not supported and traffic always has to go via some kind of gateway.
Subnets have an attribute that determines whether a network interface created in the subnet automatically receives a public IPv4 address. Therefore, when you launch an instance into a subnet that has this attribute enabled, a public IP address is assigned to the primary network interface (eth0). A public IP address is mapped to the primary private IP address through network address translation (NAT).
One important information to mention here. A public IP address is assigned from AWS pool of public IP addresses and it is ephemeral. When you disassociate it from your instance, it’s released back into the pool and it cannot be retrieved. If you require a persistent public IP address allocated to your account that can be assigned to and removed from instances as you require, use an Elastic IP address instead. For more information, see Elastic IP Addresses.
Private subnets
Similarly a private subnet is a subnet without access to the Internet. There are scenarios thought that will require access to outside world – for example to do software updates in your instances. In those cases you can configure NAT to allow communication from your instance but disallow any incoming connections from the Internet.
In AWS exists two types of NAT devices:
- NAT gateway (recommended) – redundant, managed service for NAT
- NAT instance – Linux instance that you have to configure and manage yourself
Security Groups
Security groups control inbound and outbound traffic for your AWS entities, like EC2. Consider them as firewall rules that follow your instances and control traffic. Security groups are statefull.
Network Access Control Lists
Network ACLs control inbound and outbound traffic for your subnets. You can see them as router ACL, stateless and configured on subnet level.
Example
Let’s put together all this theory, make some example and design simple two tier application.
Requirements:
- First tier must be reachable from the Internet.
- Second tier must have only access to the Internet for software updates and can’t be reached from outside (Internet).
- Application must be able to survive one AZ failure.
- Traffic must be possible only on certain ports.
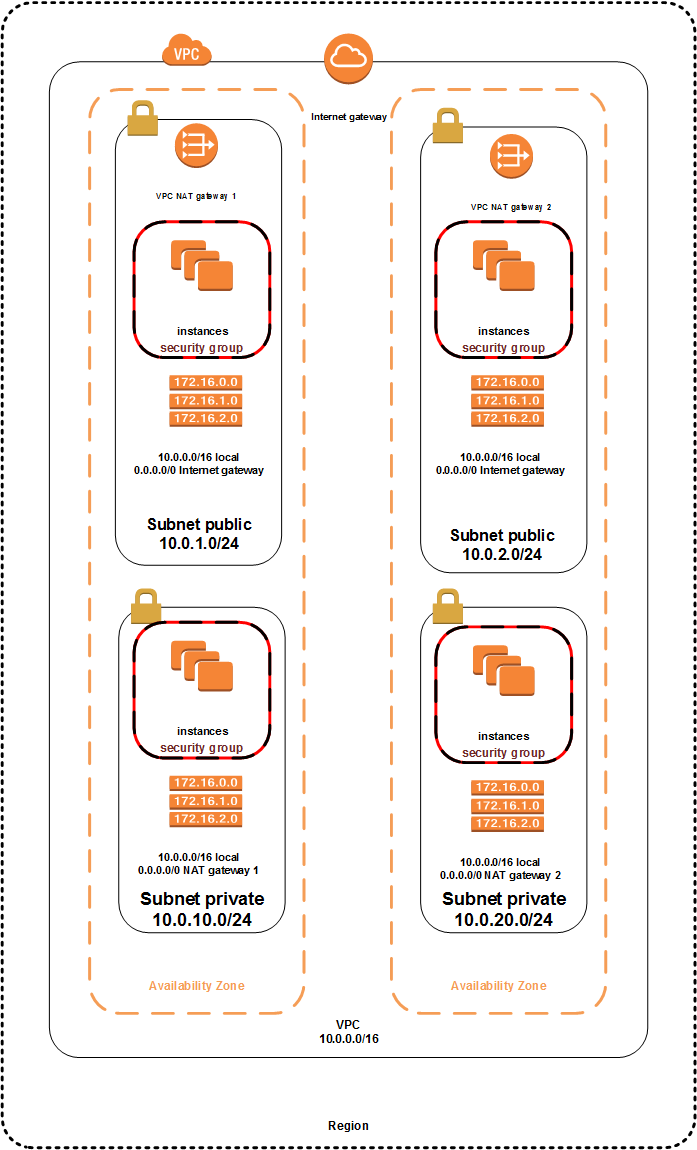
Design decisions:
- Four networks in two AZs for redundancy.
- Routing is possible in whole VPC – each routing table has entry 10.0.0.0/16 local.
- Traffic between first tier and the Internet goes via Internet gateway.
- Traffic from second tier to the Internet goes via NAT gateway located in public subnet.
- Accessible ports are configured with Security Groups. For example for first tier we can allow incoming traffic on port 80, 443 and outgoing traffic for all ports. For second tier we can allow incoming traffic only from our first tier and outgoing traffic only for IPs that we need to communicate with for software updates.
Reference Materials
AWS on the road
AWS VPC documentation
Podcast Datanauts 090: AWS Networking Deep Dive
AWS VPC Core Concepts in an Analogy and Guide

